So I went searching for alternatives and much like one of my favorite podcast from RadioLab revealed about magic tricks... The only secret in magic is that the secret must be ugly (said by Penn Jillette).
I present to you the fantastic and ugly secret of the SSLKEYLOGFILE environment variable.
So... what I stumbled upon and have been debating for over a month is a way in which you can decrypt HTTPS traffic without a man in the middle technique (Fiddler) or having the private key (old Wireshark method that is useless now). Instead, the browser does all the hard work and logs yours session key to a log file that is then easily referenced by Wireshark.
Say what?!
Let me repeat... your browser tells all your secrets and makes decrypting HTTPS traffic something that even sniveling grade school kid could do.
Before I go on... I truly hope that you will use this information for good and not evil. Because someone that is a bit creative could really wreak havoc on someone else's life without much effort. I'm telling you this, because I finally came to the conclusion that knowing this will make you able to defend yourself better.
The Ugly Secret
First off, this only works with Chrome and Firefox. Edge and Internet Explorer do not use this technique. My guess is that won't be a problem since most people seem to use Chrome these days. Start off by navigating to the "System" Control Panel applet. Select "Advanced system settings" from the links on the left.
A "System Properties" dialog box appears. Next select "Environment Variables"
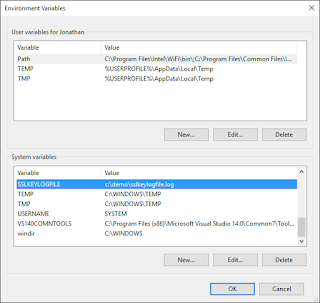
Yet another dialog box appears. The "Variable name" is "SSLKEYLOGFILE" and the value is a directory and filename of your desire. Please make note of this directory and filename for future use in the configuration of Wireshark. Click OK
View that the "SSLKEYLOGFILE" variable now appears in the "System variables" list with the correct path to the filename you specified.
Start up Chrome or Firefox and browse to a website with HTTPS capability. After doing so, you should see the log file you specified. Feel free to open it in Notepad if you want to see what is there. You'll be surprised as to how many entries appear in a short time.
Next start Wireshark (Download here if you don't have it). I'm using the Legacy UI in case you are wondering why yours might be different. Navigate to the Edit -> Preferences Menu.
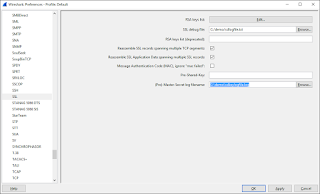
Navigate to the "SSL" Protocol and enter the directory path and filename for the log file you specified in the Envrionment Variable under "(Pre)-Master-Secret log filename". Click OK
Capturing HTTPS Traffic
So now all this is setup, what does it all look like when you do a capture? Start your Wireshark capture and browse to a website that uses HTTPS. If you want to make it easier to view the traffic you can set your Display filter to "http" and hit Apply.
You know that decryption is happening by viewing the Decypted SSL portion at the bottom of the screen. If this is not there, then decryption is not happening and you either have a packet that is not encrypted or the reference to the log file is incorrect.
So there you have it. The ugly secret your browser has. I hope you didn't read this just before bedtime.







Great blog, Jonathon.
ReplyDeleteThanks,
JeffCSP
Real nice !!! A similar bug/functionality to debug Skype4Business is heavily required as Fiddler "screws" the connection phase when using HTTPS decryption or any MiTM functionality
ReplyDeleteyea... but I seriously doubt we will get this functionality in S4B :-) Could be seen as a security risk by some customers.
DeleteIs there an option to decrypt S4b traffic when using the client or this is just to browser ?
ReplyDeleteSorry it took me awhile to reply. I thought I did and then realized I didn't. This article is just browser. I have another blog that is closer to what you need http://blog.ucomsgeek.com/2013/11/using-wireshark-to-decrypt-lync.html
DeleteCouple of things, you can no longer use the technique on the other article when you have Diffe Hellman ciphers being used. You will have to go into the registry and make sure only RSA ciphers are available. In addition, to capture SIP traffic using that method many times you have to completely exit the client, start your capture, and then start up the client in order to capture the proper key exchange to decrypt the traffic. Hope this helps.
doesnt seem to work on a server anyway. I did test on Windows 10, works great, seems like Microsoft removed the function of the variable from servers.
ReplyDeleteBoo
Interesting... I'll have to try that out. Thanks for sharing!
Delete